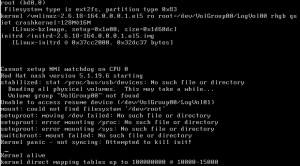
So you P2V’d a Linux box (CentOS, RedHat, Oracle, etc.) that is using LVM and now when it boots you get:
Reading all physical volumes. This may take awhile…
Volume group “VolGroup00” not found
Unable to access resume device (/dev/VolGroup00/LogVol01)
mount: could not find filesystem ‘/dev/root’
setuproot: moving /dev failed: No such file or directory
setuproot: error mounting /proc: No such file or directory
setuproot: error mounting /sys: No such file or directory
switchroot: mount failed: No such file or directory
Kernel panic – not syncing: Attempted to kill init!
Well that sucks–basically initrd didn’t have the right drivers to access the file system.
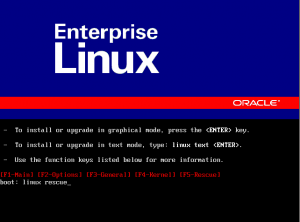 Reboot the VM with the Linux distro ISO attached
Reboot the VM with the Linux distro ISO attached
Then it boots from the CD follow the instructions to enter Linux Rescue (usually you type “linux rescue” at the boot prompt)
Now we can rebuild initrd with the missing drivers.
Enter:
|
1 |
chroot /mnt/sysimage |
|
1 |
cd /boot |
Type:
|
1 |
mkinitrd -v -f initrd |
Now hit tab and it will auto complete then add the text that was autocompleted when you hit tab except for the .img
So your command should look like:
|
1 |
mkinitrd -v -f initrd2.4.18-19.8.0.img 2.4.18-19.8.0 |
Hit enter and it will do it’s thing with a lot of output coming out, when it’s done type exit annd exit again and the VM will reboot automatically. Â Should boot up just fine this time.